
“What you don’t understand could put your identity at risk” – April 3, 2015 IDShield
When it comes to protecting personally identifiable information (PII) and reducing risk of identity theft, the more accurate information you have, the better off you are. Here I share some common misunderstandings about identity theft and explain the reality of each:
Myth1: Identity theft can be prevented completely
Reality: There is no practice or product that can wholly prevent identity theft. There are several components of your personal identity which are collected and used for many reasons. They can’t be locked down in a way that allows only you to authorize their use. Certain tools and practices go a long way to reduce the risk of becoming a victim and to notify you of fraudulent activity early but you must understand that you cannot prevent every type of identity theft.
Myth 2: I use cash and don’t use credit so I won’t become a victim of identity theft.
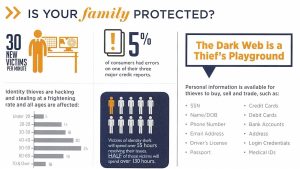
Reality: There are two things to consider: First, just because you have not established a credit account, that doesn’t mean somebody else will not use your PII to obtain goods on credit. Second, identity theft affects far more than credit. Identity theft can involve criminal acts, medical care, banking, employment and more. It is important to monitor and protect your identifying information as much as possible regardless of your favorite payment method.
Myth 3: If I become a victim of identity theft, I will have to pay the debts created by the thief.
Reality: There are federal laws that protect victims of identity theft from being held financially responsible for debts created by an identity thief. See Statement of Rights for Identity Theft Victims. However, the victim must address the misuse of their PII in a timely and complete manner with the affected entities.
Myth 4: My credit report is monitored so I don’t have to worry about identity theft.
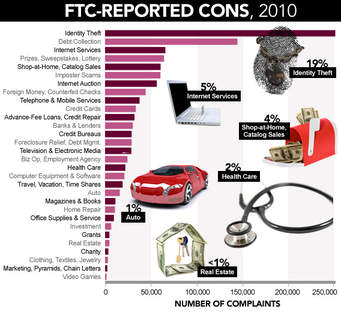
Reality: Credit report monitoring can help you discover potential credit-related identity theft early. While it may then provide an opportunity to take steps to prevent other cases of credit-related identity theft, you must approach credit report monitoring as a valuable tool of detection rather than prevention. As stated earlier, a thief can use your PII to accomplish much more than opening new credit accounts.
Myth 5: Sensitive data can be transmitted safely via e-mail.
Reality: Unless you are encrypting your email message and sending the encryption key separately, email is not a safe way to share PII. Note that legitimate organizations will not ask you to share sensitive information via email.
Myth 6: You must supply your Social Security number (SSN) if asked for it.
Reality: There are laws requiring you to provide your SSN for certain purposes but not everyone who requests your SSN is required to collect it. Entities that request your SSN for legitimate purposes include, but are not limited to: government tax and welfare agencies, financial institutions and securities brokerages, state motor vehicle departments and employers upon your acceptance of their offer of employment. See the SSA’s history page for situations that require a SSN.
Other entities may ask for it because it is a readily available identifier. Before sharing this piece of sensitive data, ask why it is needed and if there is a different identifier you can give instead of your SSN.
Myth7: Paper records (or other physical documentation) with PII are much safer than electronic records.
Reality: Stealing physical items is still a very common method of obtaining PII. Items stolen may include a laptop computer, purse/wallet, files from an office, or even trash from a home or business. Secure items holding PII to the best of your ability (locked box or desk drawer, safe or safety deposit box).
Myth 8: I shred everything so my information will not be obtained by an identity thief.
Reality: Shredding papers, disks and other items that contain PII is a great thing to do on a regular basis because it reduces the likelihood that someone will find valuable information in your trash. However, data can be captured in other ways and used for identity theft.
Myth 9: It is safe to respond to an unsolicited phone call or complete an internet form as long as you recognize the name of the company.
Reality: Because of tricks such as domain masking and caller id spoofing, it is not safe to assume that you are communicating with the entity that appears to have contacted you. Do not give sensitive information by phone or internet form unless you initiated the activity and are certain of the legitimacy of the entity with which you are dealing. If you receive a suspicious phone call or email, contact the entity that appears to have sent the communication using a phone number you obtain on your own and ask about the legitimacy of the communication you received.
Myth 10: It is okay to not check my financial accounts regularly.
Reality: Most financial institutions provide a monthly statement with the expectation that you, the account holder, will review it for accuracy. In some circumstances, you have only 60 days from the date of the statement on which a problem is found to dispute the problem with the financial institution.
Myth 11: I found an unfamiliar account on my credit report and then confirmed that it was created by identity theft. Since it was created more than 60 days ago, I am responsible.
Reality: No! Some people erroneously apply the rules related to disputing unauthorized credit card charges (as mentioned in the previous “Reality” explanation) to other types of fraud.
I will elaborate on this topic in future blogs. You can contact me at 408-309-3557 if you want more information now.
Take a look at https://www.idshield.com/?hub=trholthus to view my preferred identity theft protection program.
Send an email to me, tom@trholthus.com, with your phone number and I will call you to see what information I can send you to help you with Identity theft. Your information will never be shared.
Thomas Holthus
Business Mentor






 1. Discipline is the bridge between goals and accomplishment. ~Jim Rohn
1. Discipline is the bridge between goals and accomplishment. ~Jim Rohn
Recent Comments